Defensive Publication example
Your defensive publication should describe a part of your software and give an overview of the technical problem your software addresses. Your publication can also mention alternative and/or prior solutions if any. The publication should give enough details on how it works on an abstract level, so that another programmer would be able to make an implementation.
For this tutorial, we will take as an example a Defensive Patent Publication for Qt about which the author has blogged.
Type- Erased Container Iteration
Stephen Kelly stephen.kelly@kdab.com
January 23, 2014
Title of Defensive Publication
The idea is to get the patent examiner’s attention when reviewing a patent application relevant to the system disclosed in your publication.
If the system is solving a well known, general problem in an innovative way, your title should describe the system in abstract terms.
If the system is solving a more specific problem, it is probably better to emphasize the problem so that further patent applications aiming at solving the same problem will be compared with your publication.
For example, your title could begin like: “System for… [problem]”
Thus, the title does not have to reflect precisely what the software is, it should be general enough to be understood by the patent examiner.
Abstract
A runtime registration system is required to assign an integral value to each unique type which may be contained, and each container. This may use rtti (run-time type information) supplied by the compiler, or it may use external scaffolding. What is disclosed is a method of type erasure whereby the elements of a container may be iterated over, without static knowledge of the type of the container or the type of the elements of the container.
Keywords
Abstract or Introduction
The abstract should give a clear idea what area of technology your solution relates to and give an overview of what your solution is.
- Briefly describe the technological area in which your solution operates and point out specific issues that are hard to solve or unsatisfactorily solved that are related to your solution.
- Give examples of existing solutions to reflect the state of the art in this area of technology
- Briefly describe the trends or practices in this area of technology or other areas of technology that create opportunities for new or better solutions.
- Include a short overview of your technology by briefly describing how the solution works without giving too many details on implementation.
- Provide context:
- If your publication is strongly related to one or more existing patents, identify them in the abstract and explain how they are related to your publication.
- Briefly state where this technology could be used (i.e. mobile devices, gaming, automotive)
Keywords
A list of keywords to make the document easier to search. Pick between five tags and ten tags.
Introduction
A strong type system provides readability, safety of data interpretation and can be used for compatibility between different code from different vendors. The type of all code components is determined at time of compilation of source code and is immutable. The consumer of an instance of data must know the type of the data in order to process it. Intermediate code may transport references to data, without communicating the type of the data, by using the void pointer type. Such a void pointer may be coupled with an runtime integral value which corresponds to the strict, static type. The integral value may be used at runtime to determine the viability of interpretation of the data as a particular static type. This is already common practice.
Containers are a category of type which refer to a collection of instances of a particular element type. Containers differ in implementation details such as whether elements are stored contiguously in memory, or as a linked list for example. Containers have associated types which may be used to iterate over and process the elements in the array. Such iterator types are strongly coupled to the element type in the container. Thus, to iterate over and process the elements in a container, the type of the container must be statically (ie, at compile time) known and the type of the elements in the container must be statically known.
Problem/ Opportunity
This section helps to provide context as to the defensive publication. This is useful to give input on what the state of the art is in relation to your defensive publication.
Use this section to provide:
- Explanations and background of the problem being solved
- Description of the existing solutions
- Description on the current trends followed in this area or in other technologies that are also applicable to this problem
- Emphasis on what makes your solution stand out compared to existing solutions
Description
A runtime registration system is required to assign an integral value to each unique type which may be contained, and each container. This may use rtti (run-time type information) supplied by the compiler, or it may use external scaffolding.
What is disclosed is a method of type erasure whereby the elements of a container may be iterated over, without static knowledge of the type of the container or the type of the elements of the container.
This method is applicable to a language which:
Is statically typed
Has a way to represent data whose type is not known (eg a void pointer)
Has a way to cast/interpret such non-typed data as a particular static type, where the type is defined at compile-time.
Has a common way to represent operations on containers (eg iterators, algorithms) with “static polymorphism” - that is, the API is the same regardless of the precise type of the container or the type of the element in the container.
Has no convenient built-in to provide container abstraction features.
That includes C++, but may include other languages.
Description of your solution
This section should be clear and exact so that a “person having skill in the art a.k.a. PHOSITA” (e.g. another programmer) can implement and make use of the system described in your publication.
Description of how this invention/ idea works
It should be a few paragraphs of text. Avoid domain specific language. Say “database” instead of “MySQL” for example.
Why this is better/ more efficient/ needed over what is currently available.
In order to adequately describe an invention, be sure to discuss how each component works within the method/system by breaking the invention down into steps and diagrams. Examples of potential applications and references to compare how this invention improves on what was previously available should also be included.
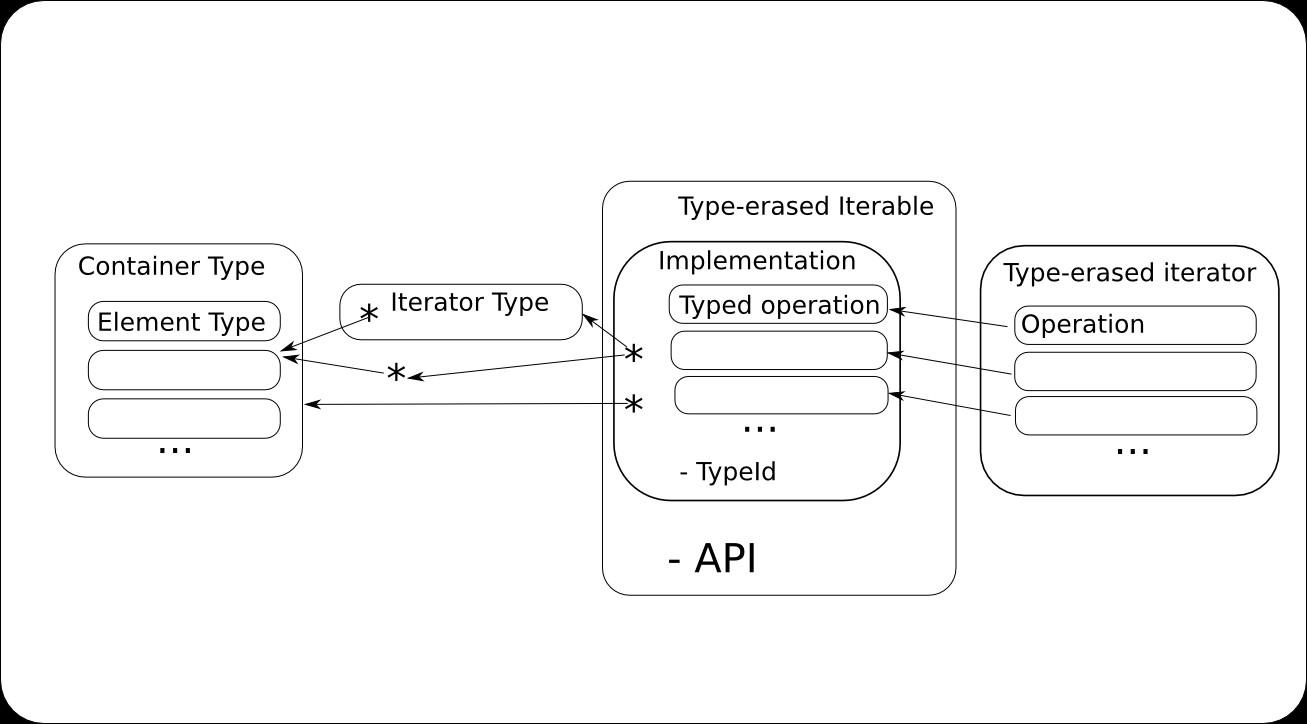
In the diagram , the strongly typed container is on the left side ‘Container Type’, and it has an associated ‘Iterator Type’.
A static
Varianttype is defined as an abstraction containing a void pointer to data and a run-time type identifier. Such a type may be created with statically typed data only. When such a type is created with data which is a container, a registry is populated to relate the run-time type identifier to a container abstraction implementation.The container abstraction implementation (‘Implementation’ in the diagram) stores a type-erased, immutable void-pointer to the container, a type-erased, mutable void pointer representing an iterator, and various function pointers for the operations (‘Typed Operation’ in the diagram) which need to be performed on an iterator to the container. Such operations include but are not limited to increment, decrement, dereference, advance, distance, comparison and assignment .
The static type used to create the
Variantinstance is also used to construct the container abstraction implementation. The function pointers in the container abstraction implementation are generated with a factory template-dependent method. The API of the pointed-to functions are type- erased.The implementation of the pointed-to functions operate on iterators and are implemented according to standards and library features for iterators, including but not limited to increment, decrement dereference, advance, distance, comparison and assignment.
There are generally two different forms of container iterators. One is a pointer to contained data, which is suitable for containers which store elements contiguously in memory. The other is a standalone type which supports the standard API required of an iterator type. The two forms are handled differently. In the first case, the type-erased mutable void pointer representing an iterator stored in the container abstraction implementation may point to the actual data in the container. In the second case, the type-erased mutable void pointer representing an iterator stored in the container abstraction implementation may point to a heap-assigned copy of the standalone type which supports the standard API required of an iterator type. The heap-assigned copy is deleted when no longer required.
An abstraction is defined which encapsulates the operations on the container iterator objects. The abstraction must handle at least assignment (which may include heap construction), deletion (in the case of heap construction only), advancing the iterator, dereferencing and comparison. The abstraction is implemented in terms of an iterator as a-pointer-to-contained data and as a standalone type. In all cases, the result of mutation is stored in the type-erased, mutable void pointer representing an iterator in the container abstraction implementation.
The container abstraction is defined in terms of the container abstraction implementation. The container abstraction (‘Type-erased Iterable’ in the diagram) contains standard methods to allow creation of type-erased iterator implementations pointing to the beginning and end of a container, as well as iterators pointing to particular seeked elements. This allows the use of standard library algorithms and language features as they apply to the containers. The Type-erased Iterator is implemented in terms of the container abstraction implementation.
Dereferencing a type-erased iterator yields an instance of a
Variant, which contains a type-erased void pointer to data in the container, and an integral value representing the type. The integral value may be examined to interpret the void pointer as a static type which can be used with other code.
Steps to create the invention
Publications and patents relevant to software will typically consist of several steps. Each step should be described in detail for this portion.
- Break down each component and describe how each component works with the overall system
- List each step in the process and describe how each step is completed.
Each of the system components should be described exhaustively
Examples
If there are any alternate uses for this invention, be sure to include them. These are potential applications that have yet to be implemented.
References
If you have references to for example a publication in a scientific journal, technical report, USENET posting, or print magazine, include it here with as much information as possible (publication number, ISBN, ISSN, etcetera). Please make sure they are clearly marked in the rest of the document.
Diagrams
- Illustrate how components interact
- Show the overall process
This can be a flow chart, a network diagram, etc.
What happens next
To get started drafting your own defensive publication, you can download our template and follow the instructions therein. You can access several sources for defensive publications on our Github page.
Once your publication has been vetted by Linux Defenders, it will be submitted to the relevant patent-related databases and on defensivepublications.org.